Twitter/X Webhooks Not Working: CRC, Secrets, and Signature Verification (A Friendly Dev Guide) 💥🧰
You’ve set up your webhook, hit “register,” grabbed a ☕… and then—silence. No events. Or worse, the dreaded “CRC validation failed.” Been there. Webhooks with Twitter/X are wonderfully fast when they work—and hilariously picky when they don’t. Today we’ll unpack the why and the how: Challenge Response Checks (CRC), secrets, signature verification, and the tiny gotchas that break everything. We’ll also compare the classic Account Activity API with the newer V2 Webhooks management flow, then share hard-won insights so your endpoint hums along smoothly. 🚀
🎬 Quick Intro: What your webhook must do (and when)
At a high level:
- Register a webhook with X (v2:
POST /2/webhooks). As soon as you do, X immediately pings your URL with a CRC GET request. Your endpoint has ~3 seconds to respond with a JSON body containing aresponse_tokencalculated using HMAC-SHA256 (key = your app’s consumer secret, message =crc_token). If you nail this, the webhook is markedvalid. ✨ (See CRC spec in the docs for exact hashing details.)
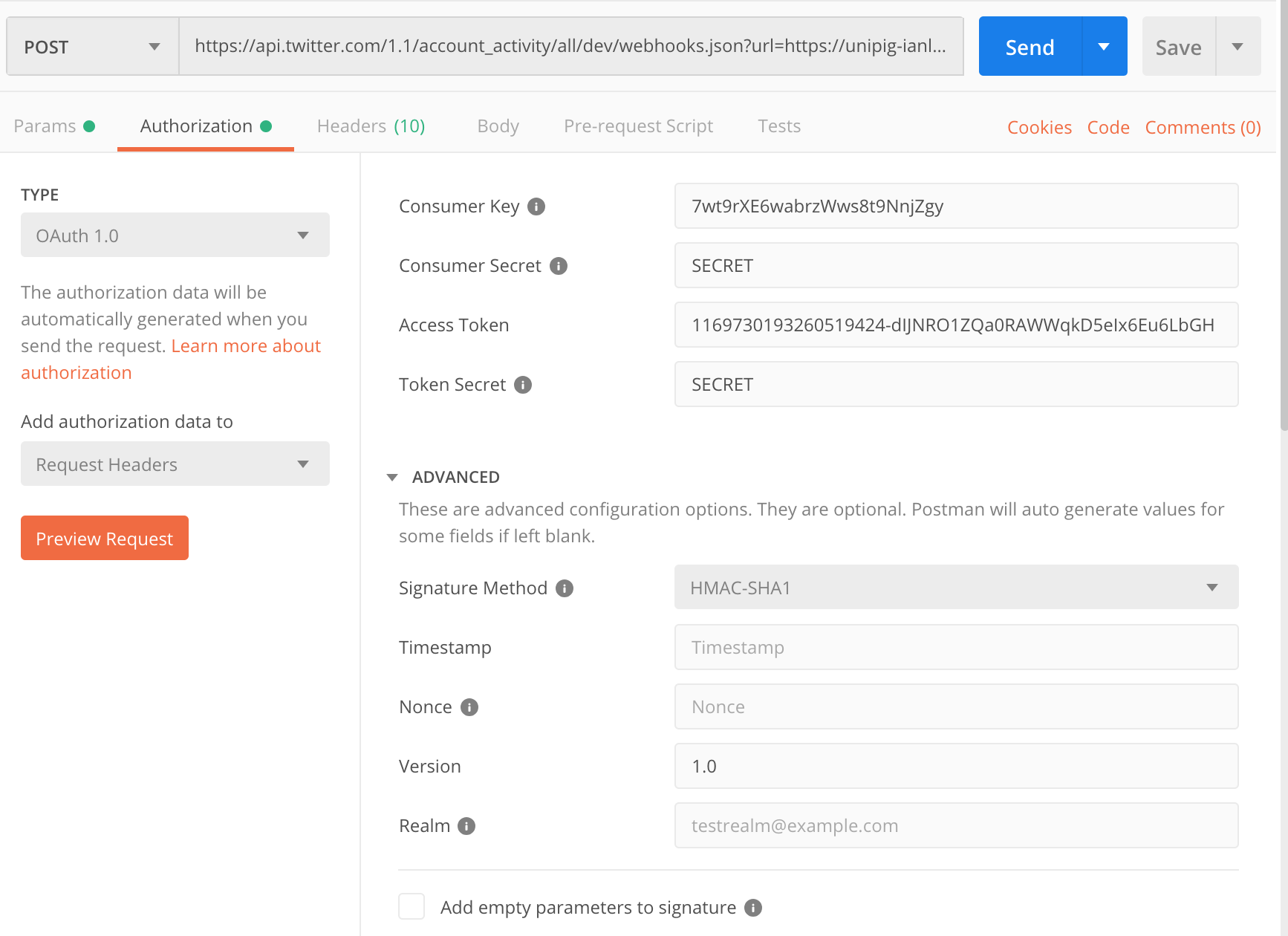
- Keep passing CRC: X will re-check hourly, and you can manually trigger a CRC (v2:
PUT /2/webhooks/:id) after deployments. If CRC fails, deliveries pause. - Verify signatures on POST deliveries using the
x-twitter-webhooks-signatureheader (HMAC-SHA256 over the raw body with your consumer secret). See Webhook security guidelines for signature details.
And yes—your webhook URL must be HTTPS and cannot include a port (e.g., :5000 won’t fly). Check the Webhooks introduction.
🥊 Comparison: AAA (v1.1/Enterprise) vs. V2 Webhooks Management
| Topic | Account Activity API (AAA) | V2 Webhooks (Management Layer) |
|---|---|---|
| What | Delivers account events (DMs, likes, follows, tweet events) | Manages webhooks: add/view/delete/validate |
| CRC | Same concept: GET with crc_token; return response_token |
Same CRC dance, now documented under V2 Webhooks |
| Signature | x-twitter-webhooks-signature HMAC-SHA256 |
Same header/verification model |
| Checks frequency | Hourly CRCs + manual trigger | Documented hourly + PUT /2/webhooks/:id |
| Pricing/limits | Enterprise AAA delivers the events | V2 page lists tiers (Pro Self-Serve, Enterprise) & # webhooks |
| Docs | Enterprise fundamentals detail CRC/signature + examples | Central intro + endpoints for POST/GET/DELETE/PUT /2/webhooks |
🧪 Example (with a tiny metaphor)
Think of CRC as the doorman checking you really belong in the building: he hands you a challenge string (crc_token), and you must hand back the right handshake (response_token = "sha256=" + base64(HMAC_SHA256(crc_token, consumer_secret))). If you answer fast (<3s) with the correct handshake, you’re in. If not, the doorman stops letting deliveries reach your door.
Textbook JSON response your endpoint must return to the CRC GET:
{ "response_token": "sha256=<base64_encoded_hmac_hash>" }
🧩 Troubleshooting Table: Why CRC & Signatures Fail (and Quick Fixes)
| Symptom | Likely Root Cause | Fast Fix |
|---|---|---|
CrcValidationFailed on POST /2/webhooks |
You didn’t return the JSON body in time, or miscalculated the HMAC, or not HTTPS | Ensure HMAC-SHA256 with consumer secret, base64, prefix with sha256=, respond in <3s, serve HTTPS |
| Hourly CRCs start failing after a deploy | New code path slow or returning wrong JSON | Test CRC handler separately; add a health check and PUT /2/webhooks/:id to re-validate |
| Signature verification fails on POST deliveries | You hashed the parsed JSON not the raw body; wrong key; or compared strings naïvely | Hash the raw bytes of the request body with consumer secret, compare with constant-time |
Webhook never becomes valid |
URL includes a port, wrong scheme, or duplicate | Remove port; ensure https://; check with GET /2/webhooks |
| You expect multiple webhooks but can’t add more | Plan tier limit reached | Check tier limits on Webhooks |
🧠 Insights (stuff that saves hours)
- Return JSON fast. If you do heavy work in your CRC handler, you’ll time out. Keep CRC minimal.
- Always verify signatures on deliveries. See the signature verification rules.
- Don’t include ports in your registered webhook URL—even if staging runs on
:3000. - Expect duplicates. De-dupe by event ID.
- Re-validate after deploys with
PUT /2/webhooks/:id. - Mind your plan: Pro Self-Serve allows only 1 webhook, Enterprise allows more.
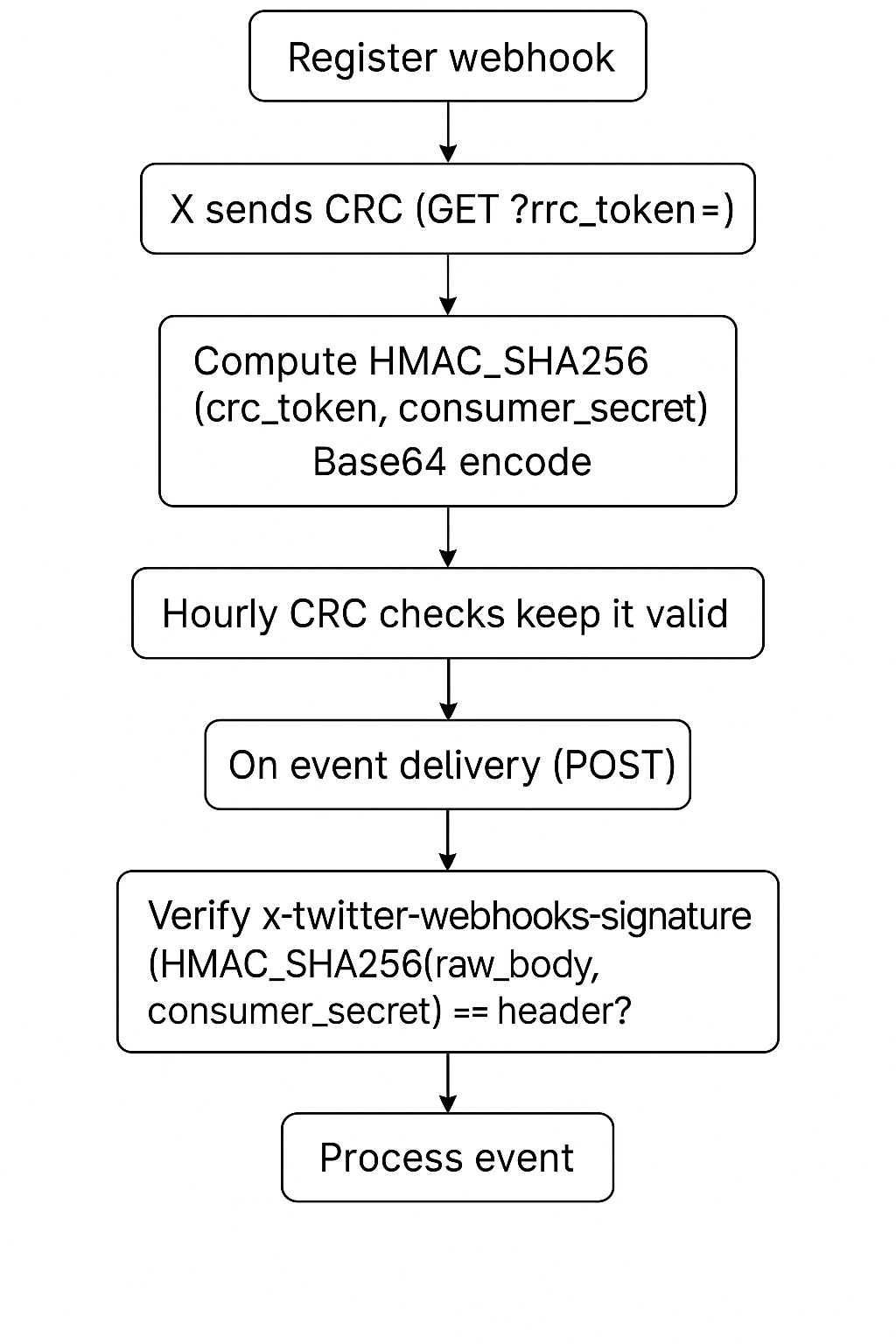
🧭 “Follow the arrows” diagram
Register webhook → X sends CRC (GET ?crc_token=...) →
Compute HMAC_SHA256(crc_token, consumer_secret)
Base64 encode → JSON { "response_token":"sha256=<...>" } → 200 in <3s
↓
Hourly CRC checks keep it valid
↓
On event delivery (POST) → Verify x-twitter-webhooks-signature
(HMAC_SHA256(raw_body, consumer_secret) == header?) → Process event
🧰 Copy-paste checklist
- ✅ HTTPS URL, no port
- ✅ CRC handler returns correct JSON
- ✅ Response <3s
- ✅ Verify signatures on POSTs
- ✅ Dedupe by event ID
- ✅ Run
PUT /2/webhooks/:idafter deploys - ✅ Check your plan limits
For deeper dives: V2 Webhooks introduction and Account Activity API security fundamentals.
🫶 Emotional wrap-up
It’s totally normal to feel frustrated when your webhook sits there like a black hole. But CRC + signature verification are predictable once you wire them up exactly as X expects. Treat CRC as a quick handshake, keep it snappy; treat signatures as non-negotiable security; and be kind to your future self with guardrails like health checks and re-validations. Your webhook will go from stubborn to silky-smooth—and your real-time features will feel ✨magic✨ to users.
You should also read these…
- noepic.com – side hustle ideas that require minimal upfront cos
- huesly.com – the future of physically crosslinked foams
- beofme.com – surprising differences between physical and chemic
- beofme.com – creating routes and route effects on instagram how
- hogwar.com – gluten free baking tips for best results
- huesly.com – die besten tipps um haarverlangerungen langer halt
- hogwar.com – algorithm and for you page issues on tiktok and so
- getaluck.com – why isnt my tiktok video on the for you page
- huesly.com – cant edit tiktok business profile
- closedad.com – tiktok friend matching errors and solving methods